JandaSec Ltd Privacy Notice and Security Policy
At JandaSec Ltd, cybersecurity and data protection are woven into the very fabric of our business. We believe that privacy and security are critical enablers of trust, and our unwavering commitment to these principles underpins every interaction and service we provide. This policy serves as a detailed outline of the key security pillars that guide our efforts in safeguarding data, in alignment with the highest international standards, including ISO27001, NIST (National Institute of Standards and Technology), and UK Cyber Essentials. We are passionate about security and data privacy and believe that privacy is a fundamental human right, especially in a digital world.
Privacy Notice
Introduction
At JandaSec Ltd, we are committed to protecting your privacy and ensuring that your personal data is handled in accordance with the UK Data Protection Act 2018 and the General Data Protection Regulation (GDPR). This Privacy Notice explains how we collect, use, and protect your personal data.
Data Collection
In priciple, JandaSec Ltd does not collect any information about site visitors, nor do we actively track visitors, however this website is hosted in AWS Amplify and so some log data will be collected by AWS. For clients we are working with there will be necessary business contact information required to do business however we will always keep this to a minumum and ensure it is respected and secured.
Website Data
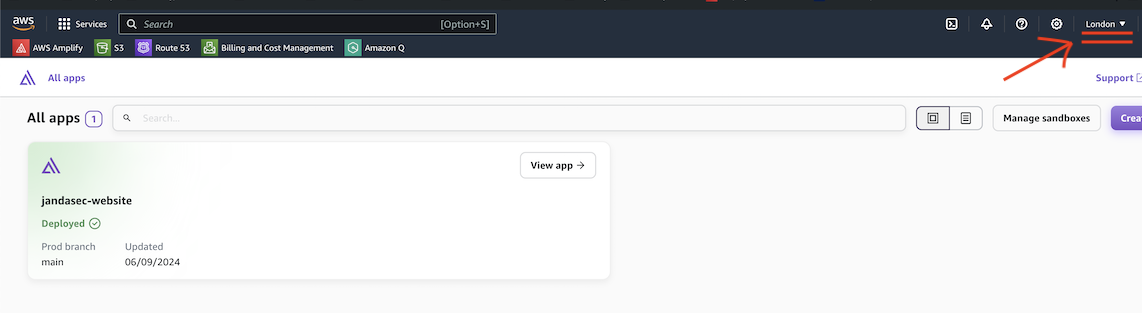
Our website, jandasec.com is hosted on Amazon Web Services (AWS), specifically AWS Amplify, in the eu-west-2 region - which is in London, UK.
For transparency, see the screenshot below from AWS evidencing that this site is hosted in the London region:
By design, jandasec.com is static site, build with Hugo. There is no ‘backend’ to the website such as APIs, databases or Lambda functions, this is an explicit security design decision and we make no attempt to capture and store any of your data.
This is further emphasised by our commitment to not use cookies on this site, which you can read more about in our “No Cookies Policy”.
Even our Contact page has been explicity designed to not require you to submit any personal data to us and rely on your already existing relationship that you will have with LinkedIn.
Please see below for further details on the lenghts we have gone to to create a secure experience on this site by way of evidence of our commitment to Cyber Security best practices.
Though our website, jandasec.com, does not attempt to collect any data, for transparency, we are hosted on AWS Amplify which uses AWS Cloudfront as a CDN by default. AWS does not collect any Personally Identifiable Information (PII) but it does log request data for technical and security purposes, which will include detalis such as:
- Page visit URL
- IP Address
- User Agent
None of this data identifies you personally as the site visitor and JandaSec does not make any use of this logging data.
For further details about AWS Security and Compliance programs please see here.
Client Data
When working with clients, we collect basic business contact information, which may include:
- Name
- Business Email Address
- Business Phone Number
- Company Name
This data is used solely for the purpose of conducting business with our clients and is stored securely. You can read below how as a business we operate to keep this data secure.
Suppliers
We collaborate with various suppliers to provide this website and our services to clients. Details about our suppliers, their geographical locations, and their security controls are as follows:
| Supplier | Geolocation | Security Controls | PII | Reason |
|---|---|---|---|---|
| AWS | London, UK | https://aws.amazon.com/security/ | NO | Website hosting |
| BitBucket (Atlassian) | Global | https://www.atlassian.com/trust | NO | Website code repository |
| Proton | Switzerland | https://proton.me/mail/security https://proton.me/blog/switzerland | YES - Business contact data | Encrypted Business Email, Documentation and Calendar |
| SendSafely | USA | https://www.sendsafely.com/security/ | No | Encrypted business file transfer |
| Signal | Global | https://support.signal.org/hc/en-us/categories/360000674811-Security | No | Business mobile messaging |
| NordVPN | Global | https://nordsecurity.com/ | No | Secure Internet Connectivity |
Data Protection Requests
You have the right to access, correct, and delete your personal data or to make a data protection complaint. You may also request to exercise your “right to be forgotten” or file a subject access request (SAR). To submit any such requests or ask about your data protection rights, please Contact Us.
Security Policy
Introduction
At JandaSec Ltd, we are obsessed with maintaining the highest standards of security. Our commitment to cybersecurity is reflected in our robust security measures and adherence to best practice principles.
Security Pillars and Principles
Confidentiality
We ensure that data is accessible only to those authorized to view it. Our security practices include:
- Use of strong encryption protocols for data in transit and at rest.
- Access controls and authentication mechanisms.
Integrity
We safeguard the accuracy and completeness of data through:
- Regular audits and monitoring of data integrity.
- Implementation of data validation processes.
Availability
We maintain the availability of our systems and data by:
- Implementing redundant systems and backups.
- Ensuring timely patching and updates of software.
Security Controls
Our security controls which are based upon the aforementioned principles are defined between the security controls of this website and the security controls we operate as a business.
Website Security Controls
Cryptography
At JandaSec Ltd, we recognize the critical importance of securing data in transit. To achieve this, we enforce robust TLS (Transport Layer Security) protocols—specifically, TLS 1.2 and TLS 1.3—across all our web applications, along with enforced HTTPS connections and strong cipher suites. These measures form a fundamental part of our commitment to ensuring the confidentiality, integrity, and authenticity of all communications on our platform.
Why Robust TLS 1.2, TLS 1.3, Enforced HTTPS, and Strong Cipher Suites Matter:
Protection of Data in Transit: TLS 1.2 and 1.3 provide end-to-end encryption, ensuring that sensitive information—such as personal data, financial details, and authentication credentials—is protected from unauthorized interception or tampering during transmission. This safeguards against common threats like man-in-the-middle (MITM) attacks.
Adherence to Modern Security Standards: TLS 1.2 and 1.3 represent the latest cryptographic standards, offering superior security over outdated protocols like TLS 1.0 and 1.1, which have known vulnerabilities. By using these modern protocols, we ensure that our security is aligned with industry best practices and compliance requirements, such as ISO 27001, GDPR, and PCI DSS.
Enforced HTTPS for Secure Communications: HTTPS is enforced throughout our website to guarantee that all traffic is encrypted. This protects our users from insecure connections and enhances privacy by ensuring that all interactions with our platform are secure. We implement HTTP Strict Transport Security (HSTS) to ensure browsers only interact with our site over HTTPS, preventing protocol downgrade attacks.
Strong Cipher Suites for Enhanced Security: Cipher suites are essential in determining how encryption is handled between our server and clients. By using strong cipher suites, we ensure that encryption algorithms and key lengths provide maximum protection against cryptographic attacks. We regularly review and update our cipher suites to eliminate weak ciphers such as RC4 and 3DES, ensuring we remain resilient against emerging threats.
Performance and Efficiency with TLS 1.3: TLS 1.3, the latest iteration of the protocol, offers performance improvements by reducing handshake latency while simultaneously providing enhanced security features. This results in faster and more efficient encrypted connections without compromising on security.
Authenticity and Trust: Robust TLS and HTTPS mechanisms ensure that our users are always connected to the legitimate JandaSec Ltd site and not a fraudulent or malicious site. This provides assurance of authenticity and helps build trust with our users, clients, and partners.
Preventing Data Manipulation and Replay Attacks: TLS protocols ensure data integrity, meaning the information sent between our users and our servers cannot be tampered with or altered during transmission. This is crucial for protecting our users from data manipulation, session hijacking, and replay attacks.
At JandaSec Ltd, enforcing TLS 1.2 and 1.3, combined with HTTPS and strong cipher suites, is a core part of our cybersecurity framework. These measures are essential to protect data in transit, meet compliance standards, and provide a secure and trustworthy environment for all our users.
As mentioned above in the Privacy Notice, this website is hosted in AWS Amplify in the London region. This is a static site which hosts no data and does not issue any cookies to clients. Nevertheless, we ensure a secure browsing experience by enforcing https and supporting TLS 1.3 and TLS 1.2, but nothing lower, with the latest cypher suites and state of the art configuration.
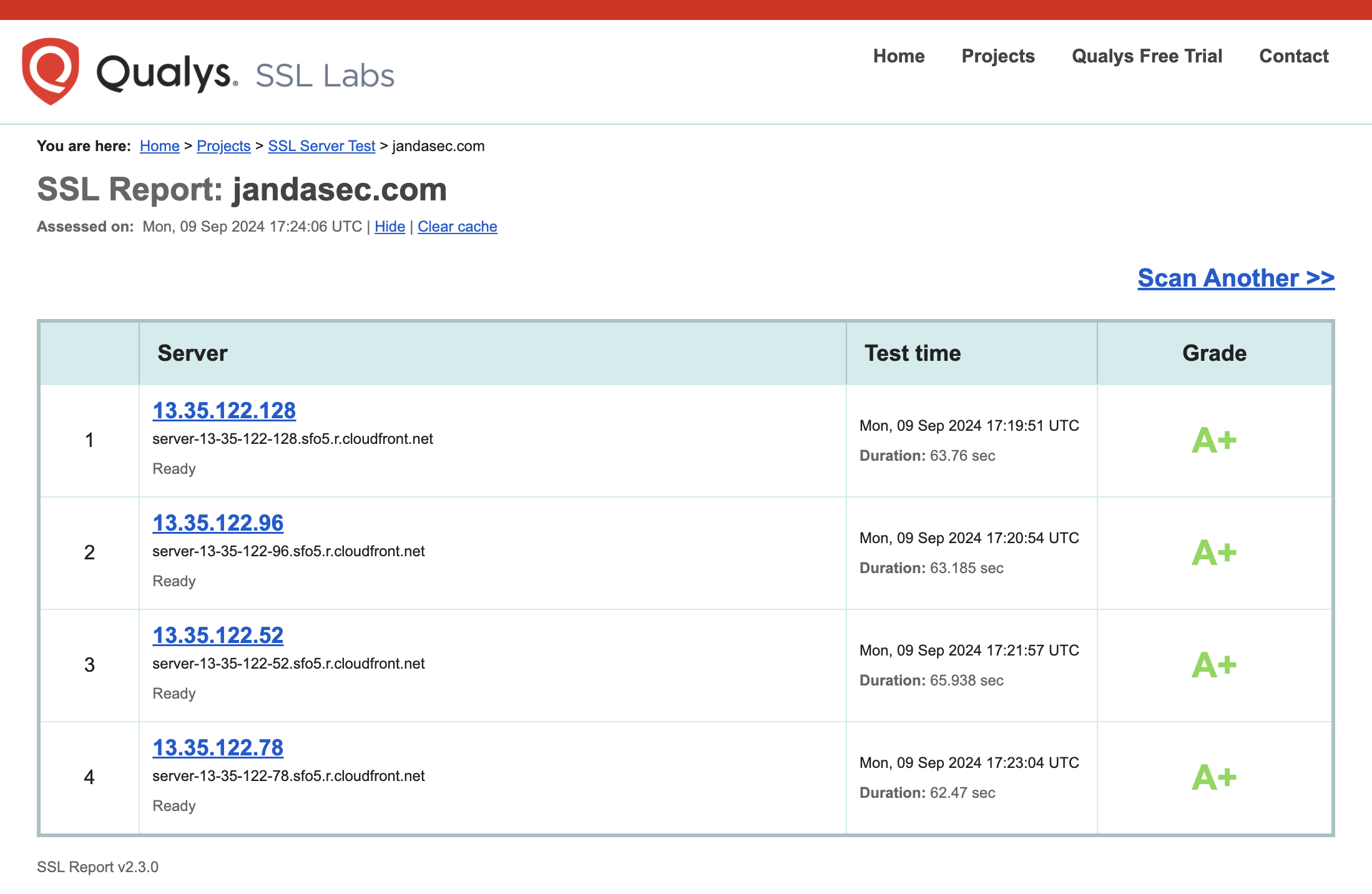
This is evidenced by running an SSL Labs Test (provided by Qualys) on jandasec.com which gives a Grade A+ score on the TLS configuration.
This first screenshot evidences the Grade A+ for each elastic IP address serving the site:
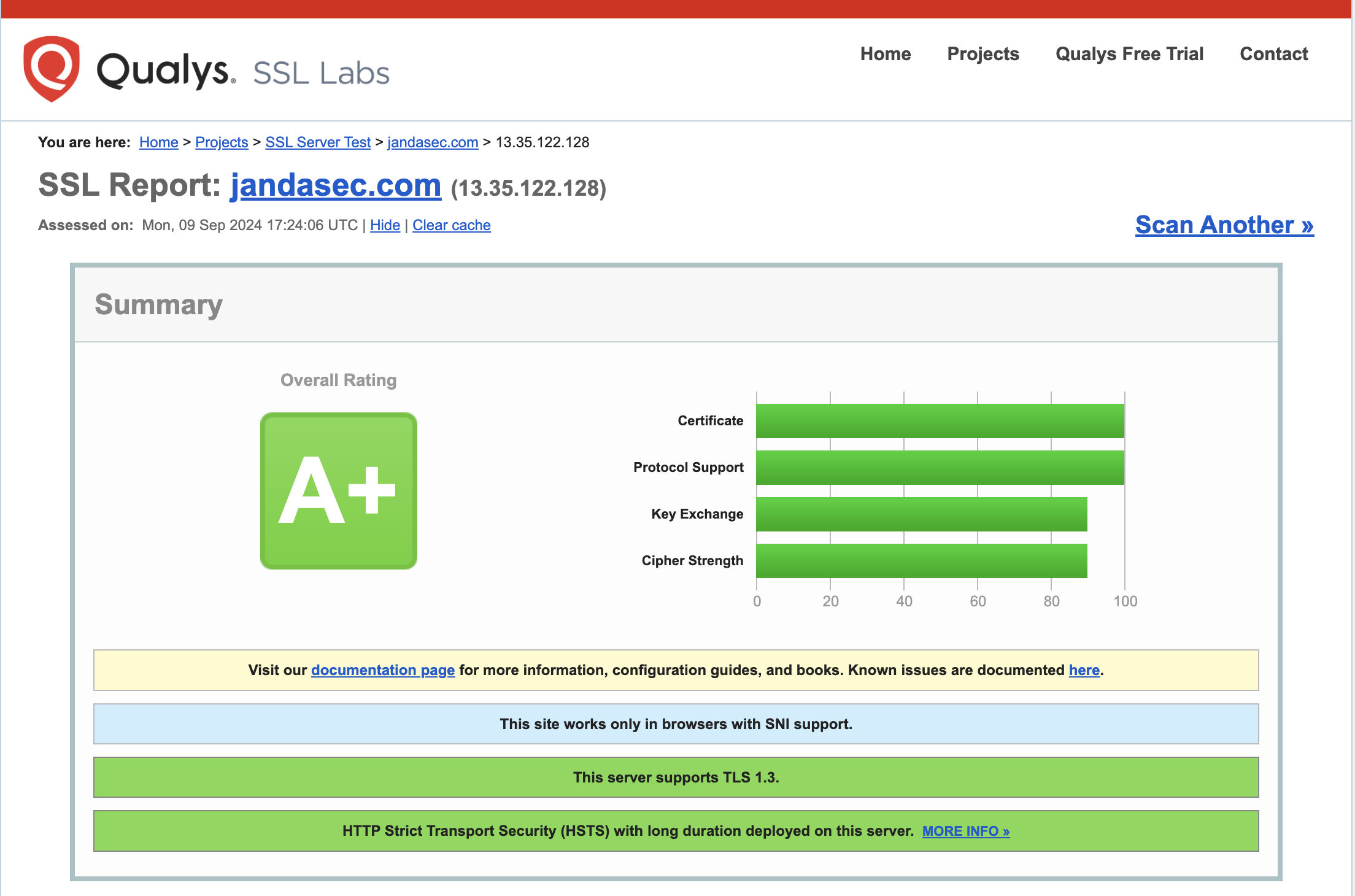
This second screenshot provides further details of the A+ result:
A full scan report for one of the elastic IP addressess serving the site can be downloaded from here.
As you can see from the above link, we do store some files that are in the public domain, in AWS S3 too. The permissions to these files are tightly controlled through explicit bucket policies and are fully encrypted at rest using AWS managed keys, and over the web, using https. All files are also stored in the AWS London Region of AWS S3:
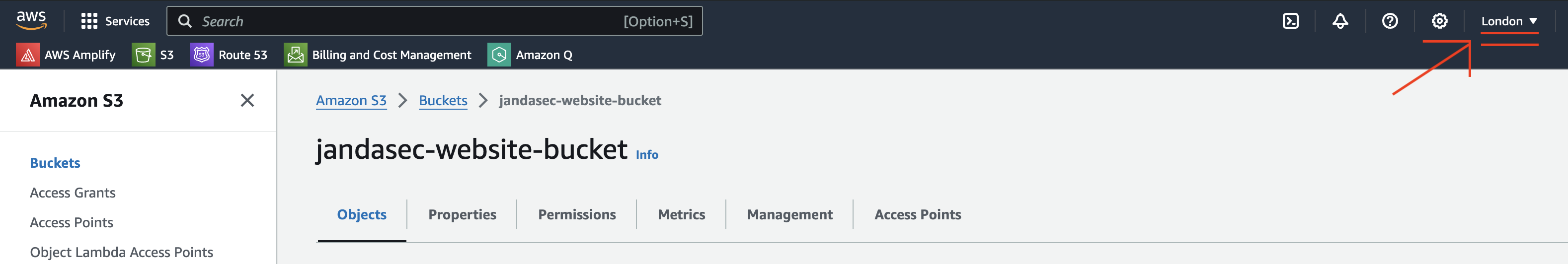
HTTP Security Headers
At JandaSec Ltd, we prioritize the security and privacy of our users, clients, and partners by implementing robust security controls across all our digital assets. One essential layer of our security strategy is the use of strong HTTP security headers, which play a critical role in protecting web applications from various threats.
Why Strong HTTP Security Headers Matter:
Mitigating Common Web Attacks: HTTP security headers help safeguard our website against some of the most prevalent web attacks, including cross-site scripting (XSS), clickjacking, and other code injection vulnerabilities. Headers like Content-Security-Policy (CSP) and X-Content-Type-Options are specifically designed to prevent these attack vectors.
Enforcing Secure Connections: With Strict-Transport-Security (HSTS), we ensure that all communications between users and our website are transmitted over encrypted HTTPS connections, reducing the risk of man-in-the-middle attacks and eavesdropping.
Controlling Browser Behavior: Headers like X-Frame-Options and Referrer-Policy allow us to control how our website is displayed in the user’s browser, ensuring that our content cannot be embedded in malicious sites and that sensitive information isn’t unnecessarily exposed in HTTP referrer headers.
Enhancing Data Integrity and Privacy: Security headers ensure that the integrity and confidentiality of the data transmitted to and from our website are protected. By using headers like Permissions-Policy, we limit the data that our site can access, such as location and camera permissions, enhancing user privacy.
Compliance with Industry Standards: Implementing strong HTTP security headers aligns us with industry best practices, such as ISO 27001 and GDPR, and helps demonstrate our ongoing commitment to maintaining a secure and trustworthy platform.
Providing Evidence of Our Security Posture: HTTP security headers provide transparent, verifiable evidence of our commitment to website security. We regularly review and update these headers to ensure compliance with the latest security standards, ensuring a safe and reliable experience for all users.
At JandaSec Ltd, strong HTTP security headers are not optional—they are a crucial part of our proactive defense against modern web-based threats. By maintaining rigorous security standards, we continue to build trust and provide robust protection for our digital infrastructure.
This is evidenced by running a secrityheaders.com scan on jandasec.com which gives a Grade A score on the HTTP Header configuration:
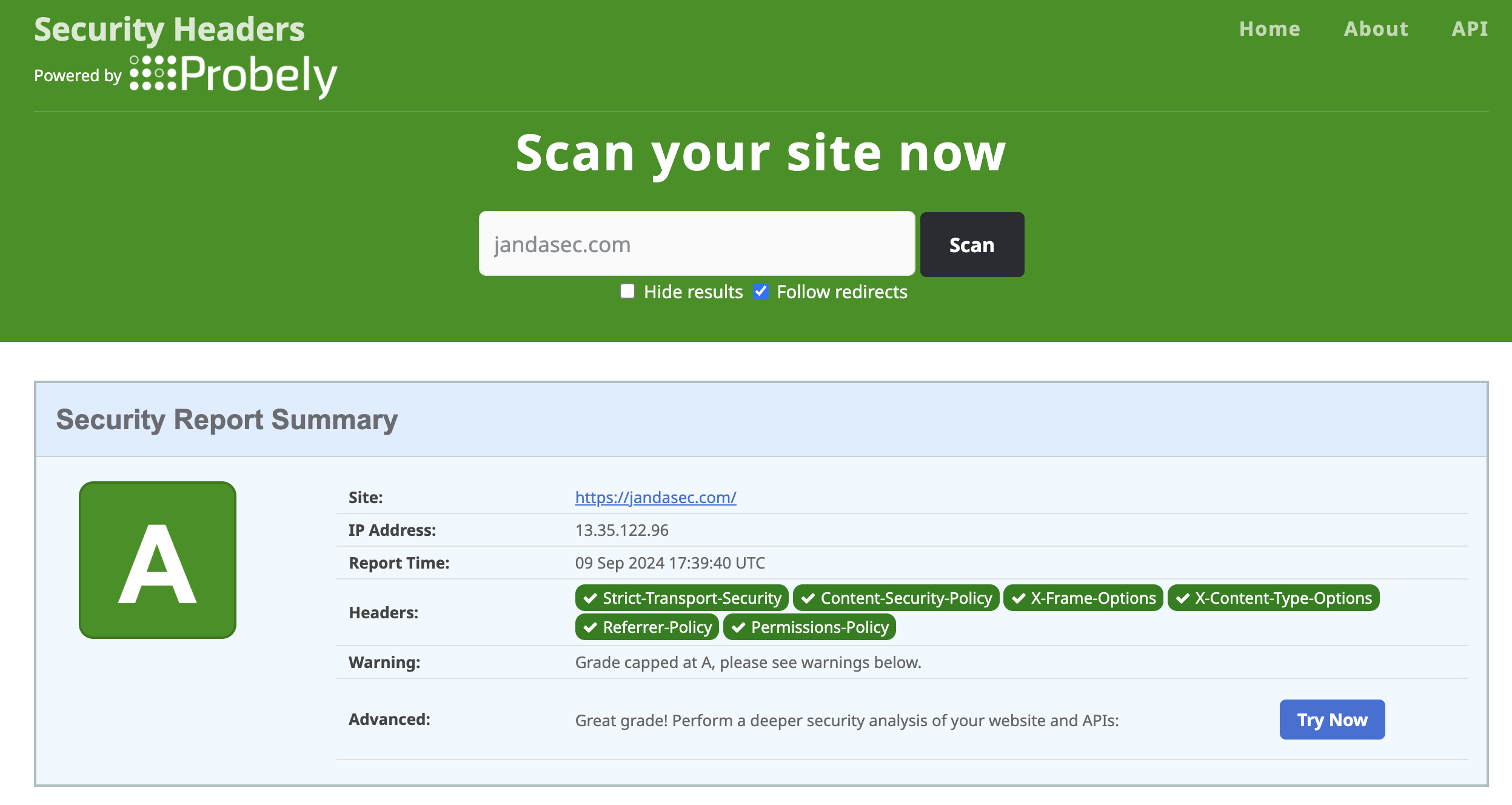
A full scan report for the HTTP Headers scan of jandasec.com can be downloaded from here.
AWS Access Control
At JandaSec Ltd., we adopt a Zero Trust approach to access control within our AWS environment, ensuring that no entity—whether inside or outside our network—is trusted by default. Access to AWS resources is governed by Role-Based Access Control (RBAC), ensuring each user only has the permissions necessary to perform their designated tasks. We enforce the following access control mechanisms:
Unique, Highly Complex Passwords: All user accounts require complex, unique passwords to minimize the risk of brute-force attacks and credential compromise.
Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second factor of authentication, such as a one-time passcode, in addition to the password. This reduces the likelihood of unauthorized access, even if credentials are compromised.
Strict RBAC Enforcement: By following the principle of least privilege, users are assigned specific roles that grant only the necessary permissions for their responsibilities. This reduces the risk of internal threats and limits the potential damage from compromised accounts.
Zero Trust Architecture: In line with the Zero Trust model, every access request is fully authenticated, authorized, and encrypted, regardless of its origin. This means continuous validation of user identities and devices before granting access to any AWS resources.
Benefits of this Security Control:
- Enhanced Protection Against Unauthorized Access: Zero Trust principles combined with complex passwords and MFA ensure that access is highly resistant to both external and internal threats.
- Minimized Attack Surface: RBAC, combined with Zero Trust, limits access to sensitive AWS resources, ensuring that even trusted users are continuously validated.
- Adaptive Security Posture: By implementing Zero Trust, we continuously monitor and assess access requests, ensuring that any unusual behavior or risk can be mitigated in real-time.
- Audit and Compliance: These controls are essential for demonstrating compliance with security frameworks like ISO27001, NIST, and GDPR, providing a clear audit trail and accountability for access management.
These access control measures, grounded in Zero Trust, ensure that JandaSec Ltd. maintains a secure and resilient environment for managing AWS infrastructure, reducing risk and strengthening compliance.
Business Security Controls
Cryptography
At JandaSec Ltd we ensure that every device, communication all storage, especially clound storage is fully encrypted to the latest standards and that keys are effectively managed:
- All devices, whether laptops or mobile devices have encryption at rest enforced by default
- All secrets, such as passwords, keys and certificates are stored encrypted, making extensive use of a robust industry leading password manager
- For secure file transfer with clients, we use the supplier SendSafely, who are mentioned above in the Suppliers list. They provide full end to end encryption of all files and messages transferred.
- For secure mobile messaging we exclusively use Signal, who are mentioned above in the Suppliers list, due to their obsession with privacy and encryption.
- For Business email, document storage and calendar services we use Proton, who are mentioned above in the Suppliers list because they are also obsessed with privacy and encryption and due to their geo location being in Switzerland all data protection is held up against Swiss privacy laws.
The benefits of which are:
- Data Confidentiality: Encryption ensures that sensitive data is unreadable to unauthorised individuals, protecting personal and corporate information from theft, breaches, or leaks.
- Compliance: By encrypting data across all channels and storage mediums, JandaSec ensures compliance with regulatory frameworks such as GDPR, ISO27001, and other international standards that mandate data protection.
- Zero Trust Environment: Encryption plays a key role in our Zero Trust architecture, ensuring that data is protected at all stages, regardless of where it resides or how it’s transmitted.
- Protection Against Data Breaches: Even in the event of a breach, encrypted data is virtually useless to attackers, significantly reducing the potential damage from a cyber incident.
- Preservation of Privacy: Encrypted communications ensure that sensitive discussions remain private and confidential, safeguarding the personal information of our clients, partners, and employees.
DNSSEC Policy
At JandaSec Ltd, security is at the forefront of everything we do, and we are committed to adopting industry-leading practices to protect our digital assets, our clients, and their data. To further strengthen the security of our website, jandasec.com, and our business email systems, we have implemented DNSSEC (Domain Name System Security Extensions).
Why We Have Enabled DNSSEC
DNSSEC is a critical enhancement to the Domain Name System (DNS) that protects against a range of DNS-related attacks, including cache poisoning and DNS spoofing. These attacks can result in traffic being redirected to malicious websites without the user’s knowledge. By enabling DNSSEC, we ensure that the DNS responses related to our domain are digitally signed, meaning that any queries to jandasec.com are authenticated and cannot be altered or tampered with during transit.
Security Benefits for Our Website and Business Email
Protection Against DNS Spoofing and Cache Poisoning: DNSSEC ensures the integrity and authenticity of the information provided by our DNS servers. This protects our website and email infrastructure from potential attacks that could redirect visitors or business communications to malicious actors.
Enhanced Trust and Authenticity: By cryptographically signing our DNS records, DNSSEC provides an additional layer of trust that guarantees visitors to our website and recipients of our emails are interacting with legitimate and verified JandaSec services.
Secured Business Email Communications: For clients who engage with us via email, DNSSEC ensures that our business email domain is protected against potential email hijacking or impersonation through spoofed DNS records. This provides added confidence in the integrity of our email communications.
Defense Against Man-in-the-Middle Attacks: DNSSEC helps prevent attackers from intercepting and modifying the DNS responses intended for our domain, reducing the risk of man-in-the-middle attacks that could compromise client data or redirect them to malicious sites.
What This Means for Our Clients
Enhanced Security and Trust: With DNSSEC in place, our clients can confidently access our website and email communications knowing that the integrity of DNS queries is safeguarded. This minimises the risk of being redirected to malicious websites and reinforces the authenticity of all interactions with JandaSec Ltd.
Commitment to Industry Best Practices: DNSSEC is part of our broader commitment to adhering to industry best practices in cybersecurity. As a cybersecurity-focused business, we continually adopt the latest technologies and standards to protect both our digital assets and those of our clients.
Confidence in Our Services: By implementing DNSSEC, we demonstrate our dedication to securing the online experience of our clients. This not only protects our own services but also contributes to the security of client systems that interact with us, providing peace of mind in every transaction, communication, and engagement.
The deployment of DNSSEC is a proactive measure to protect our clients and our business from evolving cyber threats. JandaSec Ltd will continue to adopt cutting-edge technologies to uphold the highest standards of cybersecurity and ensure the safety and integrity of all interactions with jandasec.com.
To evidence our DNSSEC controls in plase please see the following screenshot taken from the Verisign Labs DNSSEC Analysis Tool which demonstrates the full digitally signed DNSSEC Chain of Trust:
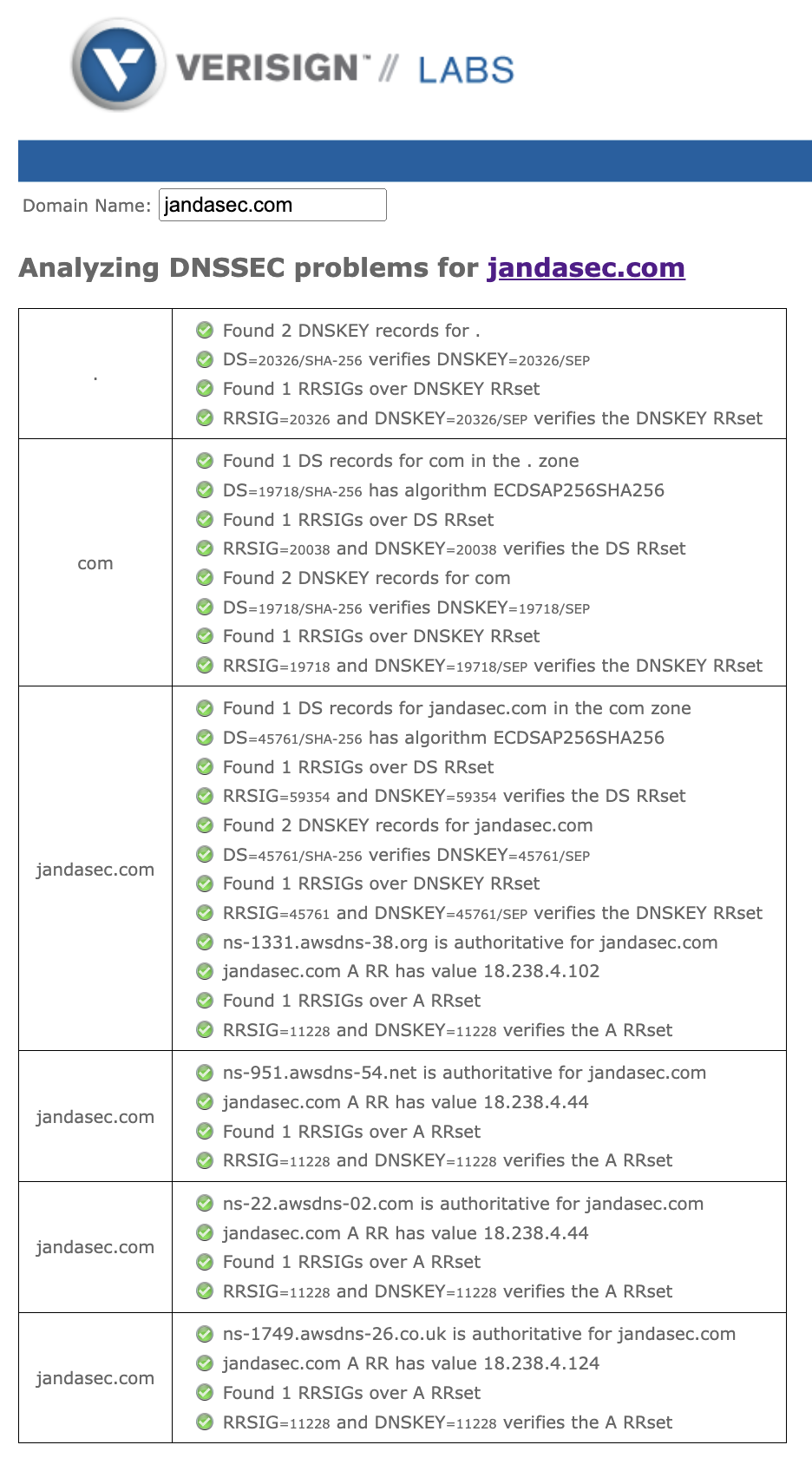
Advanced DNS Privacy and Security for Robust Threat Protection
JandaSec has deployed Quad9 as the primary DNS resolution service across all endpoints and mobile devices, as well as throughout our network infrastructure. This deployment, configured for both IPv4 and IPv6, utilises DNS over HTTPS (DoH) on individual devices and DNS over TLS (DoT) at the network level.
By leveraging Quad9’s DNS filtering, JandaSec blocks access to known malicious domains, including phishing sites and domains hosting malware, which significantly reduces the likelihood of security incidents originating from harmful web traffic. This layered DNS security approach helps ensure that network communications remain private and are only routed through encrypted channels, enhancing the confidentiality and integrity of data in transit.
Quad9 is headquartered in Switzerland, a country with strict privacy laws that align with global data protection standards, making it an ideal choice for secure and privacy-focused DNS resolution. By leveraging Quad9’s Swiss-based infrastructure, JandaSec benefits from enhanced privacy protections that safeguard DNS query data, further reinforcing our commitment to respecting user confidentiality and aligning with international best practices for data privacy.
As a best practice, this configuration aligns with industry standards and supports our ongoing commitment to cybersecurity excellence, demonstrating our proactive stance in safeguarding both our network and our clients’ data. This robust DNS setup showcases JandaSec’s dedication to implementing advanced, resilient security measures that exceed conventional security protocols.
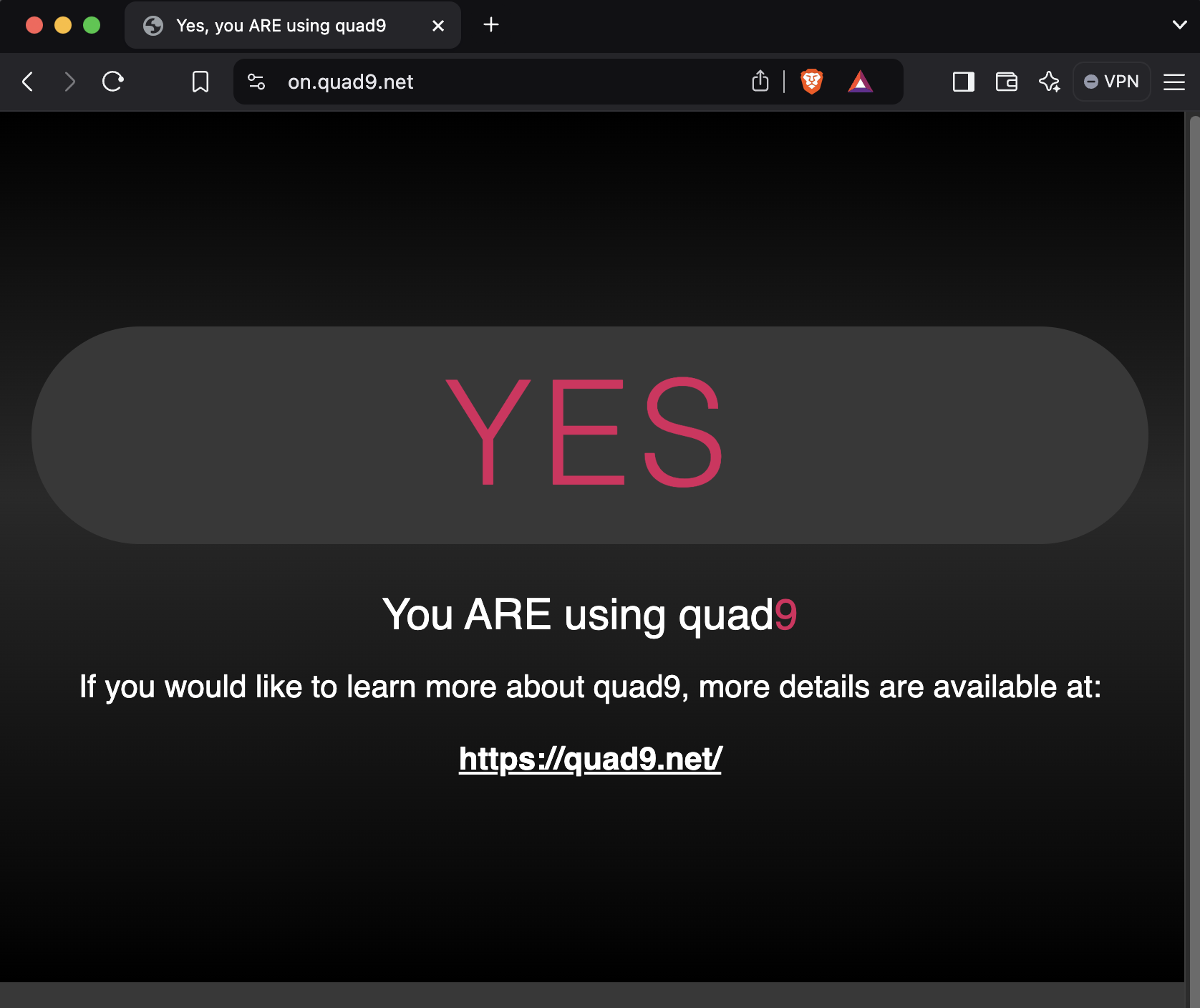
Business Email Security
At JandaSec Ltd., the confidentiality and security of email communications are of utmost importance. We use Proton Mail, a secure email service that not only provides end-to-end encryption but also complies with Swiss privacy laws, which offer robust protection for user data.
To ensure that all email communications with JandaSec are secure and protected from potential cyber threats, we enforce the following email security measures:
Email Privacy and Encryption:
End-to-End Encryption with Proton Mail: Emails sent between Proton Mail users are encrypted at every stage, ensuring that no unauthorized third party can read the contents. Proton Mail’s encryption ensures the confidentiality of both the message body and attachments.
TLS Encryption: For external communications, JandaSec uses Transport Layer Security (TLS), ensuring that emails are encrypted during transmission. This protects against interception and eavesdropping as the email travels across the internet.
MTA-STS: To further enforce secure communication, we have implemented Mail Transfer Agent Strict Transport Security (MTA-STS), which ensures that emails are always transmitted over a secure TLS connection, preventing downgrade attacks that could allow email interception. To see our MTA-STS policy, please click here.
Anti-Spoofing and Authentication:
DMARC (Domain-based Message Authentication, Reporting & Conformance): JandaSec has implemented DMARC to protect against email spoofing and phishing attempts. DMARC helps verify that emails claiming to come from jandasec.com are legitimately sent by us and not by malicious actors.
SPF (Sender Policy Framework): With SPF, we define which mail servers are authorized to send emails on behalf of jandasec.com. This prevents spammers from sending fraudulent emails that appear to come from our domain.
DKIM (DomainKeys Identified Mail): DKIM adds a digital signature to our emails, verifying the integrity of the message and ensuring it hasn’t been altered in transit. It helps authenticate that the message originates from JandaSec.
PTR Records: We have set up PTR (Pointer) records, or reverse DNS lookups, to further verify the authenticity of the sending server. This helps recipient servers confirm that the IP address sending emails on behalf of JandaSec is legitimate.
Why These Measures Matter:
- Confidentiality: Encryption ensures that even if emails are intercepted, the content remains confidential and unreadable without the decryption keys.
- Authentication and Integrity: DMARC, SPF, and DKIM verify the authenticity of emails sent from JandaSec, preventing fraudulent emails and ensuring the integrity of our communications.
- Protection Against Spoofing: These anti-spoofing measures help protect clients and partners from phishing attacks, where malicious actors may impersonate JandaSec in an attempt to steal sensitive information.
While email is inherently not a secure messaging platform—unprotected email is akin to sending confidential information on a postcard—JandaSec takes every possible step to mitigate these risks. Our use of encryption, along with DMARC, SPF, DKIM, and PTR records, ensures that our clients can be confident that interacting with us via email is done in the most secure way possible.
To evidence these controls in plase please see the following screenshot taken from the Email Security Check service provided by the UK National Cyber Security Centre(NCSC):
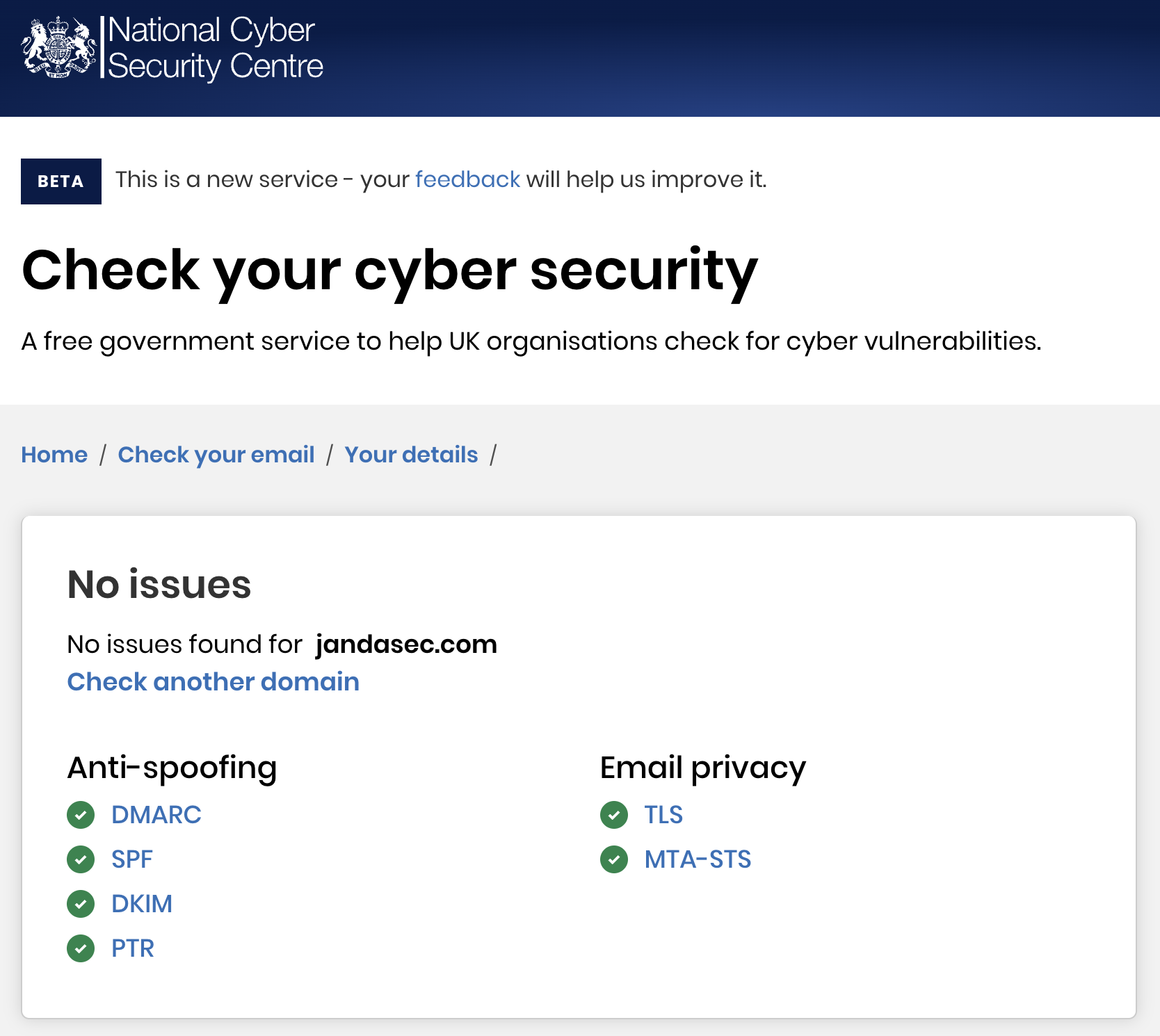
A full scan report for from the NCSC site for the Email Security Verification check, for the jandasec.com domain, can be downloaded from here.
Password Policy
At JandaSec Ltd., the security of our systems and the data we handle is of the utmost importance. Passwords are a critical component of securing our business, which is why we enforce strict policies and best practices for password creation, management, and usage. Our password policy is designed to ensure the highest level of protection for all our systems, data, and clients.
Key Controls:
Minimum Password Length, Complexity, and Entropy:
- We mandate a minimum password length of 40 characters.
- Passwords must be complex and unique, containing a combination of uppercase and lowercase letters, numbers, and special characters.
- All passwords must be randomly generated to ensure high entropy.
Why High Entropy Matters: Entropy measures the randomness of a password, with higher entropy meaning the password is harder to predict or crack. Passwords with more characters and complex combinations (uppercase, lowercase, numbers, symbols) have higher entropy, making them resistant to brute-force attacks. By enforcing long, randomly generated passwords, our policy ensures that the passwords have sufficient entropy to withstand modern cracking methods. This high level of randomness and length significantly reduces the risk of unauthorised access to our systems.
Password Storage:
- All passwords must be stored encrypted within an industry-leading password manager.
- Access to the password manager itself is protected by multi-factor authentication (MFA).
Why?: Storing passwords in a secure, encrypted vault ensures that even if a device or system is compromised, the passwords remain safe and inaccessible without the encryption keys.
Mandatory Use of Multi-Factor Authentication (MFA):
- MFA is enforced across all systems, including access to the password manager.
- We have a strong preference for app-based MFA or passwordless authentication, such as hardware tokens or biometric systems, over SMS-based MFA.
Why?: MFA adds an additional layer of security, ensuring that even if a password is compromised, unauthorized access is prevented without the second factor. App-based MFA and passwordless methods are more secure than SMS, which is vulnerable to interception and SIM-swapping attacks.
Unique Passwords for Every System:
- Passwords must be unique for every system, application, and account.
- Reusing passwords across different services is strictly prohibited.
Why?: Unique passwords ensure that a breach of one system does not compromise others. This minimises the risk of credential stuffing attacks, where attackers attempt to use stolen credentials across multiple services.
Monitoring and Dark Web Scanning:
- We continuously monitor the dark web for password leaks and take immediate action if any JandaSec credentials are found.
- Our password manager includes features that monitor password strength and score, ensuring compliance with our security standards.
Why?: Regularly checking for leaked credentials allows us to act quickly and mitigate potential damage. Monitoring the strength of passwords ensures ongoing compliance and reduces the likelihood of weak password usage.
No Password Reuse:
- Reuse of passwords across any accounts, systems, or applications is strictly prohibited.
Why?: Password reuse is a common security vulnerability that significantly increases the risk of widespread compromise if a single password is leaked or cracked.
Benefits of this Policy:
- High Entropy and Strong Defense Against Attacks: A minimum of 40-character complex passwords, combined with MFA, provides a robust defense against brute-force and credential stuffing attacks. High entropy in passwords ensures that they are unpredictable and resilient against even sophisticated cracking tools.
- Reduced Risk of Credential Leaks: By ensuring that passwords are unique, we mitigate the risk of cross-service compromise in case of a breach.
- Protection of Sensitive Data: Encrypting password storage within a secure password manager ensures that even if a device or system is compromised, credentials remain protected.
- Continuous Improvement: Monitoring password strength and dark web leaks allows us to take proactive action, ensuring that security is continuously maintained.
- Better Compliance and Peace of Mind: By adhering to these strict password controls, JandaSec ensures compliance with security standards like GDPR, ISO27001, and NIST, providing confidence to our clients that their data is being handled securely.
In today’s evolving threat landscape, password security is not just a recommendation; it is a necessity. JandaSec Ltd. is committed to the highest standards of password protection to ensure the integrity of our systems and the security of our clients’ data.
Internet Usage
At JandaSec Ltd., we prioritize secure and private internet access across all our devices to ensure the highest level of data protection and confidentiality. We enforce a stringent internet usage policy that aligns with our commitment to maintaining a secure digital environment.
VPN Use
All internet traffic from our devices—whether laptops or mobile phones—is routed through NordVPN, ensuring that all communications are encrypted and protected. We take advantage of NordVPN’s Double VPN feature, which routes traffic through multiple servers located in different countries, further enhancing security by masking IP addresses and adding an extra layer of encryption.Private Browsing
For browsing the internet, we use the Brave browser, which is designed to provide enhanced privacy and security. Brave blocks intrusive ads, prevents tracking, and helps safeguard our users’ online activities from third-party interference. This ensures that all web-based activities, both personal and professional, are conducted in a safe and secure manner.Antivirus Protection
All our devices are equipped with industry-leading antivirus software. This ensures that any files downloaded from the internet are thoroughly scanned for malicious content. If a potential threat is detected, files are automatically quarantined to prevent any risk to our systems.
Through these measures, JandaSec Ltd. ensures that all online interactions are secured and that we remain vigilant in protecting against cyber threats. Our comprehensive approach to secure internet usage is part of our broader commitment to maintaining a robust cybersecurity posture.
Conclusion
At JandaSec Ltd., we are deeply committed to safeguarding the privacy, security, and data protection rights of all individuals who interact with our website and services. Our policies reflect our dedication to upholding the highest industry standards, including strict compliance with GDPR, UK Data Protection laws, and internationally recognised security frameworks such as ISO27001, NIST, UK Cyber Essentials, and SOC2.
We take a proactive approach to cybersecurity, employing advanced security controls to protect the confidentiality, integrity, and availability of any data we handle. From the encryption of devices to the use of multifactor authentication and VPNs, we leave no stone unturned in ensuring that our systems remain secure against evolving threats.
Moreover, our commitment to transparency is paramount. By choosing not to use cookies, we respect your right to privacy and minimize unnecessary data collection. We encourage all users to review our No Cookies Policy and understand the steps we’ve taken to ensure you can browse with peace of mind.
For any questions or concerns regarding this policy or how we protect your data, please do not hesitate to contact us. Whether it’s for data protection inquiries, subject access requests, or exercising your right to be forgotten, our team is available to assist you.
As a company built on a foundation of trust, JandaSec Ltd. remains steadfast in its mission to protect your data while delivering world-class security services. We value your trust and are dedicated to maintaining the highest levels of security and compliance as we continue to grow and evolve in this ever-changing digital landscape.
Thank you for choosing JandaSec Ltd.



